Top 15 Best Devise Alternatives In 2022

Best and most demanding devise alternatives will be described in this article. Devise is a Rails authentication tool that is scalable and can be used to protect both web applications and API services. It accepts username/password credentials, token-based authentication, and account authentication utilising Facebook, Twitter, GitHub, etc.
It also includes capabilities for integrating social login, managing authentication sessions, and logging user activity. The tool comes with several adapters to help you get started quickly, but you can also easily create your own adapter if necessary. It is made to be widely extensible so that it can be used with any web application based on Rack.
There are several built-in authorities, like Admin, User, and Guest, but you may also easily establish your own if required. Encoders like ActiveRecord::Base and JSON are available for encoding and decoding user data.
Several authentication rules, including remember me, passwordless, and two-factor authentication, are also supported.
Top 15 Best Devise Alternatives in 2022
Top 15 Best Devise Alternatives are explained here.
1. Passport
Passport provides authentication for Node.js-based apps. Users can be established using a variety of techniques, including cookies, tokens, and user pools. Its modular construction enables integration into any internet application straightforward. This is another devise alternative.
It can be used to both authorise requests and create secure apps. Passport is simple to use and requires little setting; it may be used in any Express-based application. Passport supports a variety of authentication techniques, including session-based, cookie-based, and token-based.
The application supports enterprise identity providers, social networks, and other authentication techniques in addition to third-party login services like Facebook and Twitter. Also check handyman apps
Additionally, it supports a variety of authentication techniques.
2. Spring Security
The top-notch authentication and access-control framework provided by Spring Security, which provides a comprehensive security solution that tackles authentication, authorization, and security-related communications, can be used to benefit modern web applications.
Message encryption, form-based authentication, and social login are further features.
The programme is open source and distributed under the Apache 2.0 licence.
It builds on the Java Security Architecture to provide a comprehensive security solution for Java applications.
Due to the framework’s high degree of versatility, customising it to the unique requirements of your application is an easy process.
Spring Security is simple to integrate with your existing infrastructure, and you may customise security options to meet your specific requirements.
Just a handful of the several authentication options that Spring Security provides include basic authentication, form-based authentication, and Oauth2. This is another devise alternative.
You can restrict what users can do thanks to its sophisticated access control list mechanism.
Additionally, it can act as a security token service, allowing for the secure transfer of tokens across other systems.
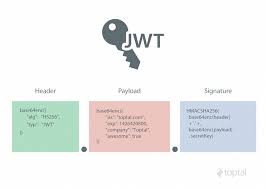
3. JSON Web Token
You can communicate data between parties as a JSON object using a common URL-safe technique called JSON Web Token (JWT).
Without the assistance of the parties making the claims, it enables independent verification of those claims.
The data structure is a JSON object with three specified fields.
The phrases “payload” and “signature” both refer to the payload’s digital signature created using JSON Web Signature, whereas the terms “header” and “payload” each refer to meta-data about the token.
This can assist in ensuring that only authorised users have access to data or resources.
Both browsers and server-side apps can use it.
Because it works with any transport protocol, including HTTP, JWT is perfect for AJAX applications.
Even if someone were to intercept the token, it would be challenging to decipher its information because JWT can be encrypted in a variety of ways.
JWT prevents tampering, making it difficult to secretly alter the token’s contents.
The security of the data transfer is enhanced by this.
4. Django REST API
JWT is a JSON-based Web application authentication solution that provides quick, secure authentication for your Django REST API. This is another devise alternative.
It uses the JSON Web Token standard to communicate data between the client and server and has built-in security features to safeguard your data.
Authentication scheme definitions are always specified as class lists.
The REST framework will attempt to authenticate each class in the list, and it will only return the value of the first class that is successful.
To use the tool, create a JSON object with the required data and sign it using a secret key.
After receiving it, the recipient can examine the signature and decipher the data.
5. LDAP
LDAP can be used in a networked environment to provide authentication and authorization services, as well as to store and retrieve information about users, groups, and devices.
Standardization, which is based on industry-standard protocols and allows it to work with a variety of software, flexibility, which enables the tool to adapt to different needs, and ease of use, which results in a simple syntax and can be accessed using a variety of tools, are some of the key characteristics.
An LDAP directory may be distributed across several servers.
The complete directory may be replicated on each server and periodically synchronised.
When a server receives a recommendation from a user, it takes ownership of it and ensures that the user receives a single coordinated response while passing it on to other DSAs as necessary.
6. OmniAuth
In order to integrate with different authentication providers, such as Facebook, Twitter, GitHub, Tumblr, and others, OmniAuth is a Ruby authentication framework for websites.
This eliminates the requirement for developers to create original code to add authentication to their web apps.
It was made to be rack-compatible, so it can be used with any Ruby web framework.
As a result of the authentication process being abstracted away, developers are free to focus on the functionality of their programme.
OmniAuth also offers a variety of other capabilities to help with authentication, including built-in support for session management and cross-site request forgery defence. This is another devise alternative.
Additionally, it includes adapters for popular Ruby frameworks like Ruby on Rails and Sinatra. You can only add the providers you require because the tool is modular in design. Overall, OmniAuth is a fantastic tool that you may take into account as one of its substitutes.
7. Firebase Authentication
A scalable token-based appointment system for your apps, Firebase Authentication offers client SDKs and backend services for authentication with various identity providers.
With the benefit of this instrument, you can quickly write a secure authentication system for your app.
The tool is easily integrated with other Firebase capabilities, such as its Realtime Database and Cloud Messaging, because to its extensibility.
You can build and manage user accounts, authenticate users using their email address and password, and do a lot more with Firebase Authentication.
In addition to Sign-In and email/password authentication, it also supports social identity providers like Facebook and Twitter.
Additionally, you can design your own unique authentication provider.
It offers libraries for well-known programming languages including Java, Objective-C, and Swift in addition to SDKs.
Overall, Firebase Authentication is a fantastic technology that you may take into account as one of its substitutes.
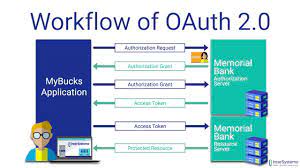
8. OAuth2
Oauth2 is a framework for web application authorization that enables safe data access without the requirement for user credentials to be stored. Additionally, it enables programmes to confirm users’ identities without requesting their passwords.
This is another devise alternative. The tool offers a few flows or techniques for authorising applications from third parties, although they are not the only ones available. Also check Library management software
Many well-known web platforms now employ Oauth2 as the industry standard for authorization. Applications can utilise it to safely access data that is kept on a user’s device or on a distant server. Oauth2 also enables programmes to exchange data without needing users to divulge their login information.
Oauth2 is based on the Oauth 1.0 standard, however it has undergone considerable revisions to fix security flaws and improve usability.
The main distinction between Oauth1.0a and Oauth2 is that Oauth2 authorises access to resources using bearer tokens rather than cookies or session IDs.
9. Oauth.io
With just a few lines of code, designers can easily add authentication or social logins to their online apps using Oauth.io, a supplier of web app integration and authentication.
It provides libraries for all the major programming languages and supports all the major providers. Additionally, you can have a strong API that enables you to integrate authentication to your own unique apps. Oauth.io has a simple setup process, comprehensive documentation, and an appealing user interface.
With a variety of authentication techniques, including passwordless, two-factor authentication, etc., it allows social login, single sign-on, and business login.
10. Sso
Sso is a user and session login authentication service that offers your users a quick and secure way to sign in to your web apps.
While offering a fantastic user experience, you can effortlessly manage user sessions, access control, and keep your user data secure. This is another devise alternative.
Both single sign-on and federated sign-in are supported, and it offers a centralised mechanism to manage the authentication process for online applications and services.
Users can be authenticated using Fso against a variety of identity providers, including Active Directory, LDAP, and others.
Additionally, Sso protects your data using secure protocols like HTTPS and TLS.
It’s perfect for businesses that need to control user access to a variety of web services.
By using the check session method, which will try to discreetly authenticate the user within an iframe, you can verify a user’s Sso status from an application.
11. OneLogin
OneLogin is a market-leading Identity and Access Management tool created specifically to make business logins easier while enhancing system security and effectiveness.
The method is used by thousands of businesses and people because it is quick and simple to set up and helps streamline many user workflows and processes, increasing productivity without compromising security.
All users, applications, and other devices are brought together in a tightly integrated cloud-based system with the aid of OneLogin.
It facilitates IAM (Identity and Access Management), making it quick and simple for users to apply your policy as intended, while lightening the strain on your IT department and allowing it to focus on its identity first strategy. This is another devise alternative.
Your staff has access to the applications that have been verified to comply with policy thanks to the system. Due to the solution’s enterprise agility and secure application access, any device in your company is protected. The entire network and organisation, including corporate workstations, web applications, and mobile devices, are subject to this protection in full.
OneLogin is a straightforward yet effective programme that controls your entire system. Additionally, it possesses a number of noteworthy characteristics that add to its allure.
12. AuthAnvil
Another programme specifically created to assist IT teams in maintaining the security of their networks, infrastructure, and devices at all times—including outside of business hours—is AuthAnvil.
One of the top platforms, it offers a variety of cutting-edge features that set it apart from rivals.
The solution relieves your IT staff of the responsibility of password management so they can spend more time making sure your networks are all operational and your data is completely safe.
The application’s biggest feature is its ability to combine password management, single sign-on, and multi-factor authentication capabilities, which effectively eliminates password bugs that both users and IT administrators encounter.
Users can easily access their accounts, data, and systems with the use of this application without having to remember their passwords.
13. TeamPassword
For software design and development teams, advertising agencies, and creative companies, TeamPassword is an all-in-one cloud-based password management system. It is a little different from it from Okta and has many more cutting-edge features, which makes it superior to others.
The solution offers effective methods for managing numerous logins and passwords.
Additionally, it makes it possible for groups, teams, and companies of all sizes to quickly manage and distribute passwords for the software, services, and tools needed to complete tasks.
Users of TeamPassword can create team passwords, specify the level of access to each password, receive notifications, and do other things.
This is another devise alternative. It is a rather straightforward tool that enables users to control, add, and distribute passwords for internal clients. Companies are able to contact with one another to discuss their initiatives thanks to this service.
One of the application’s most compelling features is its secure built-in password generator, which enables you to generate an infinite number of strong passwords.
14. WebTitan’s
WebTitan is a platform for malware protection and web content filtering that was created specifically for managed service providers, retail and public organisations that give WiFi access, Hotspot and WiFi providers.
Businesses and organisations can secure their employees and consumers when they are online thanks to this simple and one of the best deployment options that may be either on-premises or in the cloud.
It gives users the power to block access to objectionable and improper content, such as pornography, hate speech, and any other types of forbidden material.
WebTitan makes it possible to restrict the information that clients and visitors may access, guaranteeing that they are safe from all types of online dangers including viruses and phishing.
The platform has thorough reporting capabilities that help businesses create policies to provide a secure environment for their users and workers.
Similar to previous apps, it provides a number of noteworthy features, including automated scheduling, behavior-based reporting, different filters, a live view of user browsing activities, and PDF and Excel export options.
15. Teramind
Another employee monitoring tool and computer security platform is Teramind, which keeps tabs on what workers are doing online while also defending the network against potential dangers like information theft, etc.
It is one of the greatest Okta alternatives that provides all the same services while adding a few outstanding characteristics that set it apart from the contest. This is another devise alternative.
This technology allows all businesses to identify potentially dangerous security risks, isolate suspicious activities, and track staff productivity and efficiency.
By providing them with real-time notifications, the service also helps IT security and owners reduce security incidents. Also check car rental software
Teramind also locks users, and devices appear to be a danger to the organization’s credibility.
The ability to play back employee activity history allows businesses to interactively examine their employees’ activity at the rear of the day or at any moment, which is one of the application’s most interesting and enjoyable features.
The platform also has capabilities like email monitoring, keyloggers, file tracking, automated behaviour rules, and project management integration.